- Create a custom URL by adding in authentication tokens or other secrets.
- Create a custom payload body using any environment variables and specific instance variables per event. Note: that means that if you are attaching the webhook to a Group, you will be able to access Group-level variables, too.
- Debug and test the webhook in the editor by sending test messages.
Using variables
- We use the variable
JIRA_INSTANCE_URLin the URL. We previously stored this variable in the environment variables section. Alerting configurations only support the use of environment variables, secrets are not supported. - We use the variable
CHECK_IDin the payload. This is one of many event-based variables that will change with each call. See below for the complete list.
{{ }} to insert the variable.
To avoid encoding, you can access your environment variables with triple brackets, i.e. {{{USER_API_KEY}}}
You can use the following event-related variables in both URL and payload.
| Variable | Description |
|---|---|
CHECK_NAME | Full name of the check |
CHECK_ID | The UUID of the check |
CHECK_TYPE | The check type, i.e. API or BROWSER. |
ALERT_TITLE | Human readable title, e.g. ‘Check “My API check” has failed’ |
ALERT_TYPE | Type of alert, e.g. “ALERT_FAILURE”, “ALERT_RECOVERY”, “ALERT_DEGRADED”, “ALERT_DEGRADED_RECOVERY”. |
CHECK_RESULT_ID | The UUID of the result that triggered this message |
CHECK_ERROR_MESSAGE | The check error message |
RESPONSE_TIME | The reported response time for this result |
API_CHECK_RESPONSE_STATUS_CODE | The response status code, e.g. 200. Only populated for API checks. |
API_CHECK_RESPONSE_STATUS_TEXT | The response status text, e.g. “OK”. Only populated for API checks. |
RUN_LOCATION | The location where the check ran, i.e. “N. California” |
RESULT_LINK | The full link to the check result |
SSL_DAYS_REMAINING | How many days remain on the SSL certificate. For ALERT_SSL only. |
SSL_CHECK_DOMAIN | The domain of the SSL certificate. For ALERT_SSL only. |
STARTED_AT | The ISO timestamp from when this check run started |
TAGS | An array of tags assigned to the check. Have a look at our Opsgenie example below on how to render this to a JSON array. |
GROUP_NAME | The name of the group, if the check belongs to one. |
Using Handlebars helpers
We’ve extended the Handlebars templating system with some handy helpers to make our webhooks even more powerful.| helpers | description |
|---|---|
{{REGION}} | Resolves to the AWS region name, i.e. us-east-1. |
{{$UUID}} | Generates a random UUID/v4, i.e. 9b1deb4d-3b7d-4bad-9bdd-2b0d7b3dcb6d. |
{{$RANDOM_NUMBER}} | Generates a random decimal number between 0 and 1000, i.e. 345. |
{{moment}} | Generates a date or time using moment.js and allows for formatting:
|
{{moment}} helper would be setting the pagination options on a typical API endpoint:
You can find the full list of helpers in the README.md file of the underlying library we are using. For a full overview of date formatting option, check the moment.js docs.You can also use conditional helpers like
{{#eq}} statements. Here is an example:
{{#eq}} helper to execute the logic
If the ALERT_TYPE variable equals ‘ALERT_FAILURE’, print ‘DOWN’, if it equals ‘ALERT_RECOVERY’ print ‘UP’
So in the case of a failure event, the body would render to:
- You only need to create one webhook to inform a 3rd party system.
- You can translate Checkly terms to your 3rd party tool’s term for the same concept, i.e. the “up status” of a check.
Webhook secrets
You can validate each webhook we deliver to your endpoint(s). Using the optional webhook secret, you can:- Check if the webhook was sent by Checkly.
- Check if the payload was not altered in any way during transmission.
x-checkly-signature on each webhook.
On the receiving end, you can then use the value of the x-checkly-signature header to assert the validity and authenticity
of the webhook and its payload.
Have a look at the code examples below on how to use the header and your favourite web framework.
Webhook retries
Checkly will retry your webhook up to 5 times if we get an HTTP response higher than 399, e.g. a 404 or 503. Each retry is backed off 20 seconds for a total retry period of5 * 20 = 100 seconds.
This means that for checks on a 1 minute schedule, there is a potential overlap between a failure alert and recovery alert. For this
reason every webhook we send has a timestamp in the x-checkly-timestamp header. You can use this timestamp on the receiving
end to ignore any webhooks that come in “late”.
Webhook examples
The following examples give an idea how to integrate Checkly with 3rd party alerting and issue tracking systems.OpsGenie
You can create an OpsGenie alert by POST-ing the following bodyalerts API endpoint
CHECK_GROUP_TEAM variable with a different value for each Group, then modify the above snippet with the following:
PagerDuty
Given an existing service on your PagerDuty account, create an incident for it by posting the following bodyhttps://api.pagerduty.com/incidents. You will need to set the following headers:

Pushover
Send a message using Pushover by posting this body:Trello
You can create a Trello card using just the URL and no payload:SSL alert
You can send your SSL alerts using webhooks. Using the following body:ALERT_TITLE to include the domain and the days remaining till your
certificate expires.
Twilio
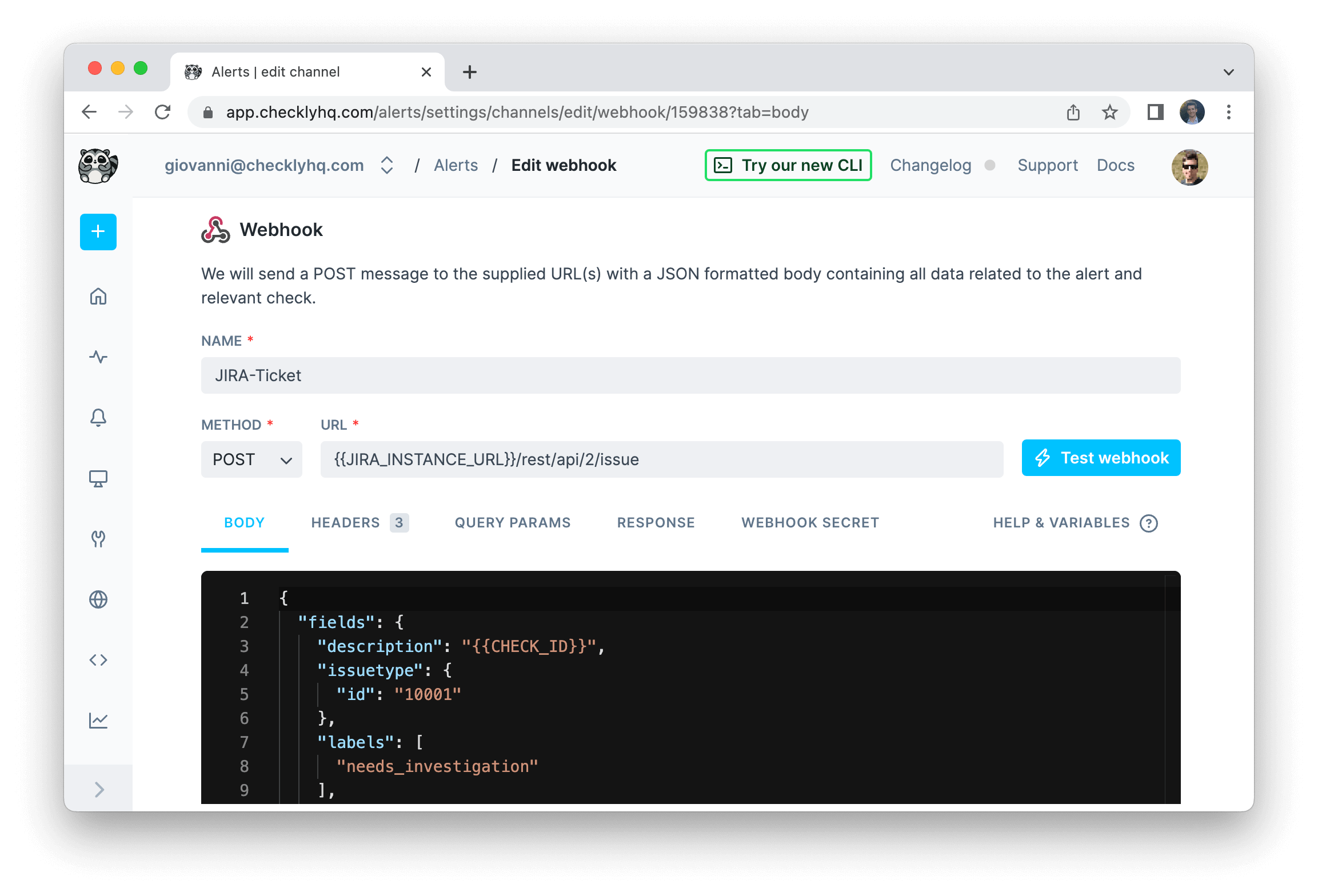
You can configure a webhook to POST to a JavaScript snippet running in a Twilio Function. This code receives the Checkly webhook JSON, then triggers a Twilio “Flow execution”:Jira
A webhook can be used to create a new issue on Jira via the Jira API, for example in the case of a previously passing check that switches to failing state. We will be creating a POST request to{{JIRA_INSTANCE_URL}}/rest/api/3/issue, where the content of your JIRA_INSTANCE_URL environment variable would look something like https://your-jira-instance-name.atlassian.net.
The required headers will be:
Body"}
{{JIRA_INSTANCE_URL}}/rest/api/2/issue). The only difference is that version 2 does not support Atlassian Document Format (ADF).