The goal: Make Playwright log into a 2FA-secured github.com account
Whether you’re building a fancy SaaS product or an e-commerce solution, security must be a major concern because you want to ensure (maybe even enforce) that your customers’ accounts are safe. Two-factor authentication is an additional way to secure all your user accounts. In a nutshell, 2FA pairs a username/password combination with another factor. This other factor could be something you know, have, or are. And while you could go the fancy route of looking into implementing iris scans or fingerprints (“something your users are”), I doubt people will appreciate your efforts. That’s why the three most common 2FA methods are SMS, native apps, or authenticator apps with software tokens. Following the flow, people log in with their credentials and are prompted with another confirmation dialog — the second factor. After receiving and entering the second-factor passcode, they can confirm that they really are the person they claim to be and access their account. And indeed, testing a passcode coming from a mobile application or SMS is challenging, but as it turns out, authenticator apps don’t include as much magic as I initially thought!Authenticator apps and TOTP
Let’s look at GitHub’s 2FA flow. When setting up 2FA with an authenticator app, the service greets you with the following screen.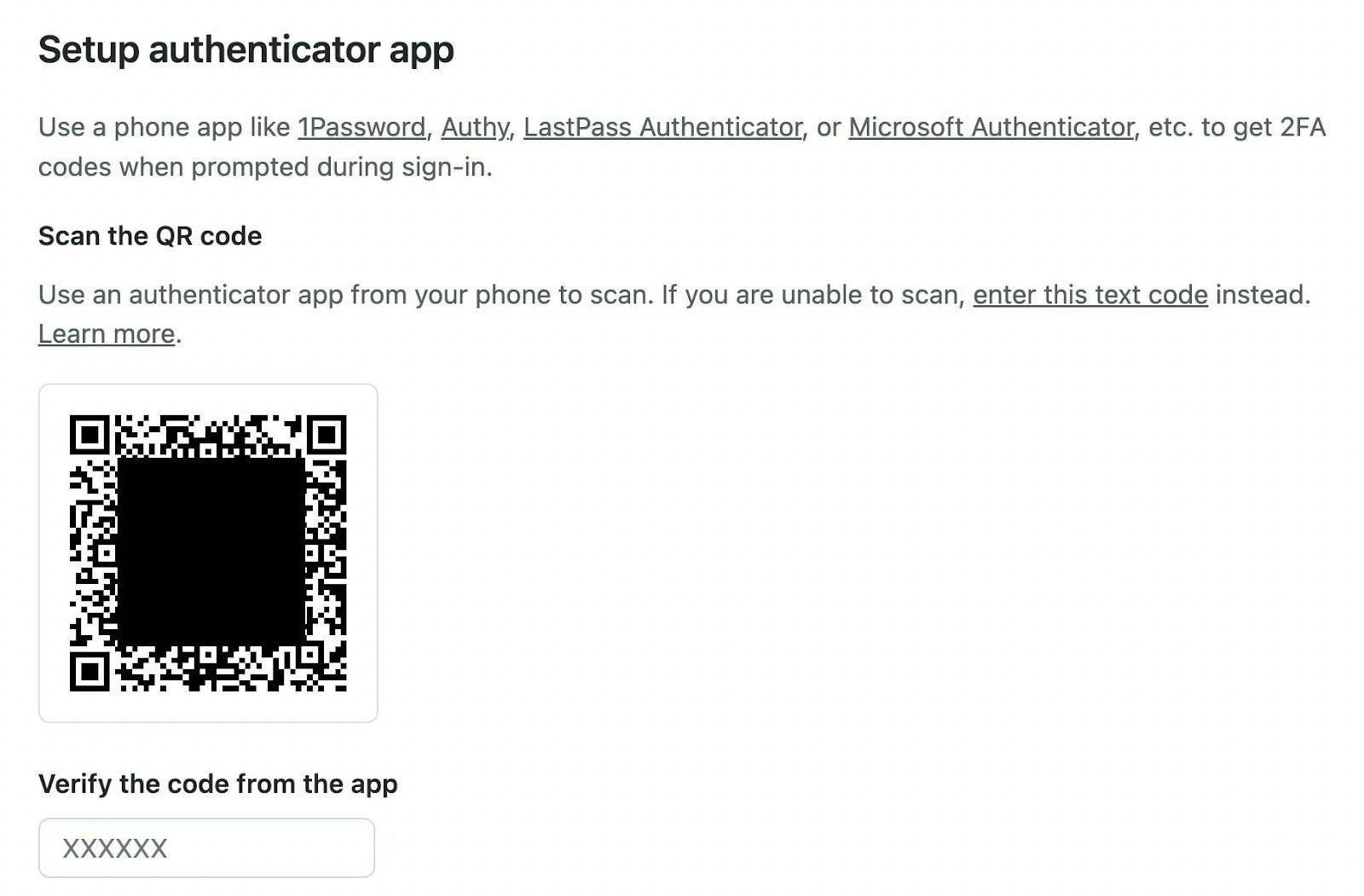
- a protocol (
otpauth) to signal that this URL should be opened with an authenticator app - the type (
totp) - a label (
GitHub:USERNAME) that is a colon-separated combination of issuer and username - a secret (
SECRET) - the issuer (
GitHub)
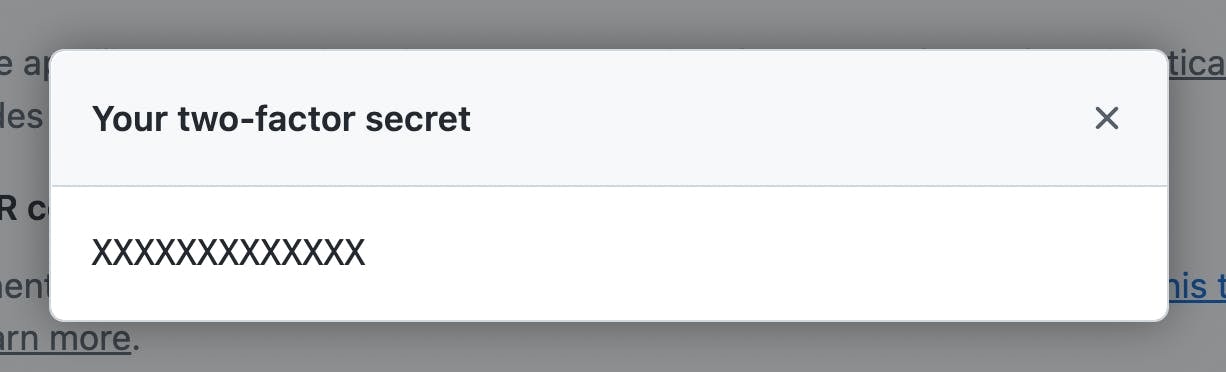
otpauth://totp/…) with an authenticator app: the app stores the second-factor secret, displays the issuer and username, and generates a new passcode every 30 seconds (30 seconds is the default but can be changed). That’s all!
You then can use the passcode as a second login factor and GitHub, as our example, can be sure that it’s you accessing your account.
To be honest, I was a little underwhelmed when I learned how this works, but it also means that this flow can easily be automated. Let’s get into some browser automation with Playwright!
Testing a TOTP login flow with Playwright
Now that you understand that TOTP flows are based on the current moment and a secret stored on a device, you can start automating it.Prerequisites
The following steps assume you have created a GitHub account, know its username and password combination, and have access to the account’s TOTP secret. If you have all this, let’s go!Setting the foundation with code generation
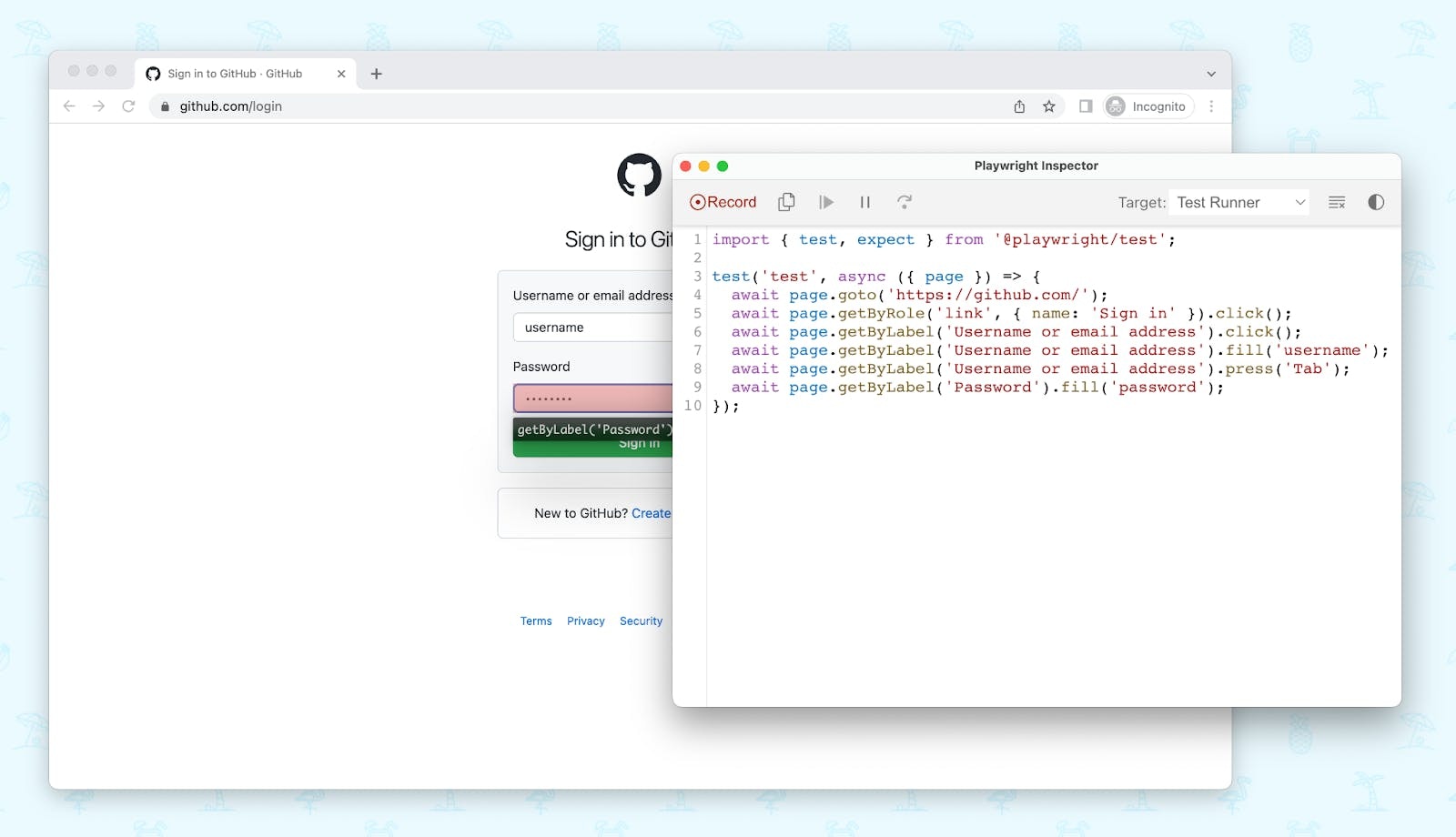
The easiest way to create a new Playwright script is by using its code generation feature.npx playwright codegen github.com
When you run this command, it will open a new browser session, and all your interactions will be recorded in the Playwright Inspector.
Using a TOTP library to generate the passcode
Luckily, the thriving npm ecosystem has a solution for every problem. The OTP Auth library has 40k weekly downloads and is in its 9th major version, which makes it a good choice that provides all the functionality to generate one-time passwords. Install it via npm:npm install otpauth
Then, initialize a new totp instance in your Playwright script…
Conclusion
I’m still amazed at how far we’ve come with the recent tooling. Playwright continues pushing out monthly releases, and I can’t wait to see what they’ll come up with in the upcoming months. But keep in mind end-to-end testing is only a tiny fraction of guaranteeing that your product is working. Third-party providers can go rogue, or your database can struggle days after you tested your deployment. That’s why I’m excited to announce that the recently released Checkly runtime (2022.10) includes the “otpauth” package and allows you to test your products at all times — even the ones that are behind a 2FA secured login! Do you want to be the first one to know when something’s off with your application? Give Checkly a try 😉.Bugs don’t stop at CI/CD. Why would Playwright? 
Sign up and start using Playwright for end-to-end monitoring with Checkly.